At the 31st ACM Conference on Computer and Communications Security (CCS), held from October 14-18, 2024, the State Key Lab of Blockchain and Data Security at Zhejiang University received two Distinguished Paper Awards. The awarded research includes "Cross-silo Federated Learning with Record-level Personalized Differential Privacy" by researcher Jinfei Liu's team and "FuzzCache: Optimizing Web Application Fuzzing Through Software-Based Data Cache" by researcher Mingxue Zhang's team. These accolades underscore significant advancements in data and network security.


Research Overview
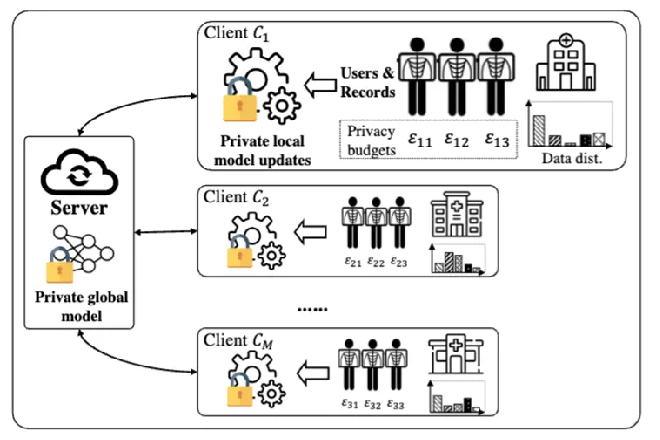
Cross-silo Federated Learning with Record-level Personalized Differential Privacy
This research, conducted in collaboration with Renmin University of China and Emory University, addresses the challenges of federated learning combined with differential privacy. Traditional methods typically apply a uniform privacy budget across records, neglecting personalized privacy needs. This paper introduces a framework utilizing two-stage mixed sampling to adapt to varied privacy requirements at both the client and record levels. It also employs an analog curve fitting strategy to optimize sampling probabilities, enhancing model utility while maintaining privacy. This work lays a foundation for future explorations in federated learning with personalized privacy protections.
FuzzCache: Optimizing Web Application Fuzzing Through Software-Based Data Cache
This research, a collaboration between the National Key Laboratory of Blockchain and Data Security and Zhongguancun Laboratory, addresses the inefficiencies in fuzz testing for server-side web applications. By implementing a software-based data caching mechanism, FuzzCache reduces repetitive data retrieval, significantly enhancing testing efficiency. The solution integrates Just-In-Time compilation technology to streamline execution and improve throughput by 3-4 times, with an average increase in code coverage of 25%. This innovation provides fresh insights into optimizing web application testing techniques.
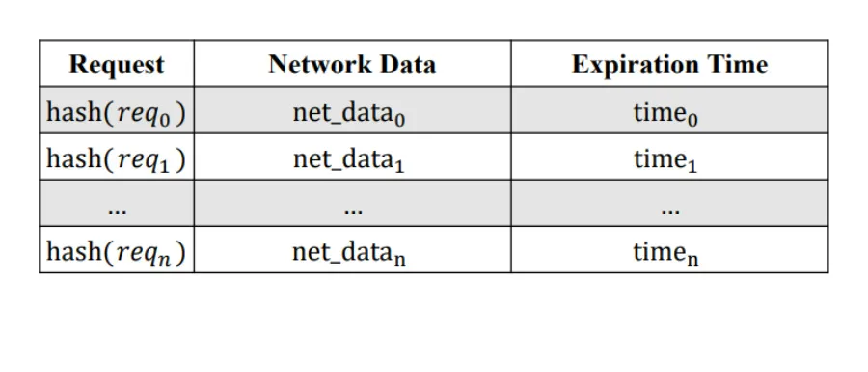
Figure 1 Network request cache structure of FuzzCache
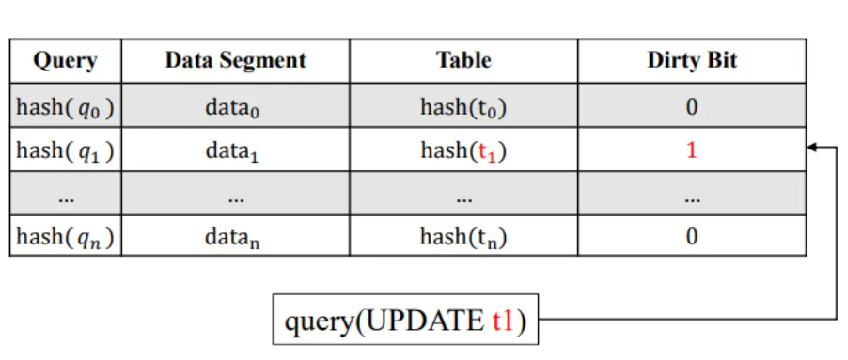
Figure 2 Database cache structure of FuzzCache
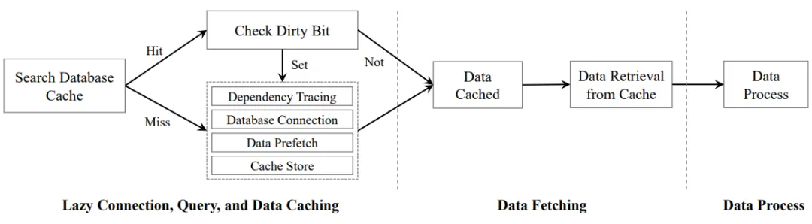
Figure 3 Execution flow of database query operation with cache






